This is no longer the latest release of ClassicPress!
You can find the latest release at the top of the Release Notes subforum.
We’re happy to announce the release of ClassicPress 1.7.1.
This release is a security release.
Minor changes and bugfixes since 1.7.0
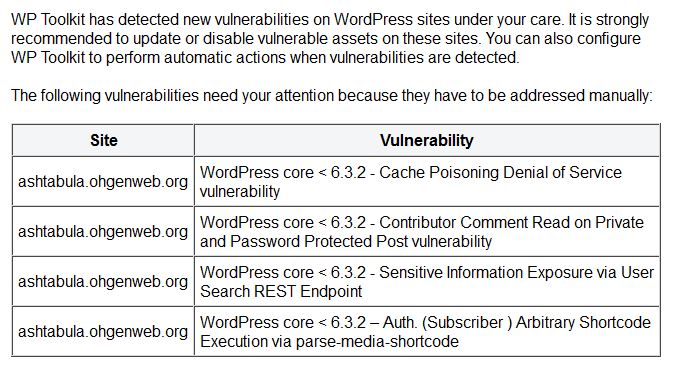
- Marc Montpas of Automattic for finding a potential disclosure of user email addresses.
- Marc Montpas of Automattic for finding an RCE POP Chains vulnerability.
- Jb Audras of the WordPress Security Team and Rafie Muhammad of Patchstack for each independently discovering an issue where comments on private posts could be leaked to other users.
- John Blackbourn (WordPress Security Team), James Golovich, J.D Grimes, Numan Turle, WhiteCyberSec for each independently identifying a way for logged-in users to execute any shortcode.
- mascara7784 and a third-party security audit for identifying a XSS vulnerability in the application password screen.
- Jorge Costa of the WordPress Core Team for identifying XSS vulnerability in the footnotes block.
- s5s and raouf_maklouf for independently identifying a cache poisoning DoS vulnerability.
Contributors
In no particular order the following people have contributed to this ClassicPress release
viktorix
mattyrob
WP Team
If your ClassicPress site has automatic updates enabled (the default configuration), then the new version will be installed automatically. Otherwise, we recommend upgrading your site(s) to 1.7.1 to receive all latest fixes and updates.
Download this release
| New sites | DownloadClassicPress-release-1.7.1.zipand follow the installation instructions. |
|---|---|
| Existing WordPress sites | Download the migration plugin and follow the migration instructions. |
| Existing ClassicPress sites | Use the built-in update mechanism (more info). |
Full changelog
The full changelog is available on GitHub.